Saturday, September 18, 2010
1.Work with your IT department
= Make sure that you install all of the patches and updates that your IT department recommends. In addition to installing Windows and Office updates, your IT department might require you to install additional security software, such as a firewall or custom software to help you connect from remote locations. Making these regular installations will keep your computer and your company's network as secure as possible.
2.Turn off your computer and disconnect
= from the network when not using the computer. A hacker can not attack your computer when you are disconnected from the network or the computer is off.
3.Do not run programs from unknown origins.
= Also, do not send these types of programs to friends and coworkers because they contain funny or amusing stories or jokes. They may contain a Trojans horse waiting to infect a computer.
4.Consider making a boot disk on a floppy disk
= in case your computer is damaged or compromised by a malicious program. Obviously, you need to take this step before you experience a hostile breach of your system.
5. Don't enable the Save Password option
= Make it mandatory for you—or someone else trying to access your computer—to enter your password on all operating system or application settings. If a dialog box prompts you about remembering the password, rather then requiring you to enter it, just choose no. Allowing the password to be saved negates having the password at all.
6.Use network file shares instead of local file shares
= Rather than opening up your computer to co-workers, use network file shares to collaborate on documents. And restrict access to the network file share to only those who need it. If you're working on a team, you have lots of other options—for example,Microsoft Share-point Workspace 2010.
7.Disable hidden filename extensions
= By default, the Windows operating system is set to “hide file extensions for known file types”. Disable this option so that file extensions display in Windows. Some file extensions will, by default, continue to remain hidden, but you are more likely to see any unusual file extensions that do not belong.
8.Review your browser and email settings for optimum security.
= Why should you do this? Active-X and JavaScript are often used by hackers to plant malicious programs into your computers. While cookies are relatively harmless in terms of security concerns, they do still track your movements on the Internet to build a profile of you. At a minimum set your security setting for the “internet zone” to High, and your “trusted sites zone” to Medium Low.
9.Use Care When Downloading and Installing Programs
= When you buy an appliance, you give little thought to it doing you or your house any harm. Why? Because there are organizations like Underwriters Laboratories that set standards and certify products. When you see a certifier’s label, you have more confidence that a product will be safer than a competing product that does not carry the same label. You’re willing to accept the risk because you believe the product has met some standards and has been certified by a respected authority.
10.Lock your computer when you leave your desk
= If you're going to be away from your desk for a while, make sure your computer is locked.
TO lock your computer:
1.On your keyboard, press CTRL+ALT+DELETE at the same time.
2.Click Lock this computer (Lock Computer if you're running Windows XP).
3.To unlock your computer, press CTRL+ALT+DELETE and enter your password.
Sunday, September 5, 2010
ARTICLE 1
= Declaration of Basic Policy. – It is the policy of the State to protect the interest of the consumer, promote his general welfare and to establish standards of conduct for business and industry. Towards this end, the State shall implement measures to achieve the following objectives:
a. protection against hazards to health and safety;
b. protection against deceptive, unfair and unconscionable sales acts and practices;
c. provision of information and education to facilitate sound choice and the proper exercise of rights by the consumer;
d. provision of adequate rights and means of redress; and
e. involvement of consumer representatives in the formulation of social and economic policies.
Reaction
=The country's official name is the Republic of the Philippines and Poverty in the Philippines is a huge problem with many different causes. The Philippine Aid Society was founded to fight poverty in the Philippines. Its mission statement is "to provide critical...
I. FEASIBILITY STUDY
II. NETWORK NEEDS ANAYLSIS
III. HIGH-LEVEL NETWORK DESIGN
IV. DETAILED DESIGN DOCUMENTATION
V. COST-BENEFIT ANALYSIS
FEASIBILITY STUDY
Situation in which the Project Exists: This proposal is for a data communication network to serve the Rock Valley National High School education system. The Rock Valley National High School recently approved funding sufficient to pay for the development of this proposal. Pending proposal acceptance by the Rock Valley National High School Education Office of Technology (a department within the state Office of Education), funding will be sought to implement the proposal.
Network Scope: The proposed network is designed to serve the Rock Valley National High School .Each district office contains four departments to be served. The Rock Valley National High School is located in Makilala North Cotabato City, 30 miles from the state office. Note that this network does not serve instructional needs of students; other resources have been allocated for that purpose. This network is for administrative purposes and is specifically designed to be independent of student computing facilities.
Objectives of the Network. The network is designed to achieve several specific business/operational objectives:
1. Secure Service: The main objective of this network is to provide secure administrative computing service to the State Office of Rock Valley National High School. It is designed to be functionally and physically isolated from access by people not employed by the Rock Valley National High School education system so as to minimize the risk of unauthorized use.
2. Integration and Update: Presently there are many LANs in the Rock Valley National High School education system, but much of the equipment is out of date, many of the LANs are incompatible with each other, and not connected in a system-wide network. This proposal describes a WAN that integrates and updates these LANs to support productive collaboration across the system.
3. Versatile Information Processing: The network will enable users to retrieve, process, and non-ASCII text, still graphics, audio, and video from any connected computer.
4. Collaboration: The network will combine the power and capabilities of diverse equipment across the state to provide a collaborative medium that helps users combine their skills regardless of their physical location. A network for this educational community will enable people to share information and ideas easily so they can work more efficiently and productively.
5. Scalability: The design of Rock Valley National High School is scaleable so that more district offices can be added as funding becomes available without having to redo the installed network.
Intended Users. The primary users of the network at the state level will be the three administrators, three secretaries, ten members of the Curriculum Department, eight members of the Human Resource Department, six members of the Finance/Accounting Department, and three members of the Computer Services Department. At the district level the primary users will be four administrators, four secretaries, four members of the Computer Services Department, sixteen members of the Human Resource Department, and two members of the Finance/Accounting Department. Parents, pre-service teachers, teachers, and the public are secondary users of the network in that they will receive information produced on the network, but they will not directly use the network.
Design Assumptions. This design assumes the following:
1. The Rock Valley National High School Education Network has a firewall that protects all information coming and going from the network.
2. Internet service is provided by the State Education Network, which is subsidized by the state government.
NETWORK NEEDS ANALYSIS
Data Types. The types of data served by the network will be reports, bulletins, accounting information, personnel profiles, and web pages. The majority of the data will be text (ASCII and non-ASCII), but there will be some still graphics and possibly a small amount of voice and video (primarily for PC-based teleconferencing).
Data Sources. Data will be created and used at all end stations on the network. The data will be produced by software applications in Windows 2000, primarily Dream Weaver and Office 2000 Professional (Word, Excel, Access, PowerPoint, and Outlook). Other data sources to be supported on at least a limited basis will Windows 2000 Accessories (Paint, Notepad, etc.), NetMeeting, Media Player, and PhotoShop. Note that the network will be not be accessible from outside…
Numbers of Users and Priority Levels. At the state level, the users will be Student, administrators, secretaries, and members of four departments. At the district levels, the users will be Student, administrators, secretaries, and members of three departments. The maximum estimated number of users on the network at any given time is 100: 25 regular users in the Rock Valley National High School and seven otherwise unanticipated users.
Three priority levels will be supported: management (top priority), user (medium priority), and background (low priority). Note that these designations do not correspond to administrative levels in the Rock Valley National High School education system; rather, they are network service levels. Network management processes will receive top-priority service; most network processes will receive medium-priority service; a few processes (e.g., e-mail transfers, backup, etc.) will be given low-priority service. It should be noted that network management will usually consume a small amount of the available bandwidth; this means that management and user processes will usually enjoy identical support. Background processes will also usually receive more than adequate service, but they will be delayed as needed to maintain support for management and user services.
Transmission Speed Requirements. The network is to be transparent to the users. Thus, remotely executed applications, file transfers, and so forth should ideally appear to operate as quickly as processes executed within an end-station. Interviews with users to ascertain their needs and expectations indicate that an average throughput of 25 mbps per user within each LAN and 15 mbps per user between LANs will more than support the needed performance in most cases (teleconferencing being the possible exception).
Load Variation Estimates. Interviews with users and observation of LAN use at the three locations yielded data on hourly average and peak loads from July to August, 2010. The data are tabulated in the appendix. The data indicate that the highest average traffic volume will occur from 7:00 a.m. to 5:00 p.m., Monday through Friday. The peak network traffic volume is expected at two times during the day: 7:00 a.m. to 12:00 noon and 3:00 p.m. to 5:00 p.m. At night and on weekends the network traffic is minimal except for the daily backups of the PCs to the LAN servers in the districts and several batch data transfers anticipated from the Rock Valley National High School. The data indicate the following network design parameters:
• The average required throughput on any LAN during work hours (7:00 a.m. to 5:00 p.m.) will be only about 0.1 mbps.
• The average required throughput on the WAN during work hours (7:00 a.m. to 5:00 p.m.) will be only 0.03 mbps.
• The peak expected traffic load on any LAN will be about 8.4 mbps.
• The peak expected traffic load on the WAN will be about 6.4 mbps.
Storage Requirements. Storage requirements need to be large enough to store all student, teacher, and state data (note: student data are data about students, not data generated by students). Interviews and observations of users’ present and anticipated storage requirements indicate that each user will need an average of 100 MB of server space (in addition to secondary storage on local PCs); the maximum estimated server-side storage requirement per user is about 1 GB. Additionally, the network operating system will occupy about 300 MB on each LAN server. Taking price-performance issues into account, each PC will have a minimum storage capacity of 10 GB, each LAN server will have a minimum storage capacity of 20 G. The Rock Valley National High School will have a 30 GB capacity.
Reliability Requirements. In keeping with user expectations and industry standards, both the LANs and the WAN are expected to operate at 99.9% uptime and an undiscovered error rate of .001%.
Security Requirements. A firewall will be used so unauthorized users will be restricted. Part of the security will be Users accounts and passwords that will give limited access. There will be different access capabilities for network managers and users.
Existing Network. There is no existing network.
Saturday, August 14, 2010
How new technology is rewiring our Brains?
=You think your car radio is broken because it doesn't display the name of the song and the artist. You tap a word on a paperback and wonder why the definition doesn't automatically pop up. You swipe a digit across the screen of your cell phone and all you get are fingerprint smudges.
Then you remember: That isn't a satellite radio. You're reading an actual book, not a Kindle. It's not a smart phone, it's a dumb one. You were expecting the cool capabilities of new technology--from old technology.
"It used to be we wanted to keep up with the Joneses," says Christine Louise Hohlbaum, author of The Power of Slow: 101 Ways to Save Time in Our 24/7 World. "Today all we want is to keep up with our gadgets. Technology pervades every aspect of our lives. Our touchscreen existence has literally rewired our brains. Our behavior is also informed by the technology we use. We tap, ping, and Skype, all day long."
So sometimes we get a little flummoxed when confronted by something that isn't digital--like a door that actually requires a key, or a book whose pages don't turn by themselves, or a TV that plays shows in real time with no skipping past the commercials.
Is this a common problem, or are we just spoiled geeks? We asked around. Turns out we're not the only ones who regularly have out-of-technology experiences. Here are some typical ones.
1.What is Outsourcing?
= Outsourcing refers to a company that contracts with another company to provide services that might otherwise be performed by in-house employees. Many large companies now outsource jobs such as call center services, e-mail services, and payroll. These jobs are handled by separate companies that specialize in each service, and are often located overseas.
There are many reasons that companies outsource various jobs, but the most prominent advantage seems to be the fact that it often saves money. Many of the companies that provide outsourcing services are able to do the work for considerably less money, as they don't have to provide benefits to their workers and have fewer overhead expenses to worry about.
2.What are the advantages and disadvantages of outsourcing?
= Advantages of Outsourcing The benefits of outsourcing are:Less capital expenditure - For example, by outsourcing information technology requirements, a company does not have to buy expensive hardware and software.
Less management headache - For example, by outsourcing business process such as accounting, a company no longer has to hire and manage accounting personnel.
Focus on core competencies - Outsourcing non-core related processes will allow a business to focus more on it's core competencies and strengths, giving it a competitive advantage.
Disadvantages of Outsourcing
Before deciding on outsourcing your company's business process, keep in mind the disadvantages of outsourcing:
Less managerial control - It may be harder to manage the outsourcing service provider as compared to managing your own employees.
Outsourcing company goes out of business - If your outsourcing service provide goes bankrupt or out of business, your company will have to quickly transition to a new service provider or take the process back in-house.
May be more expensive - Sometimes it is cheaper to keep a process in-house as compared to outsourcing.
Security and confidentiality issues - If your company is outsourcing business processes such as payroll, confidential information such as salary will be known to the outsourcing service provider.
3.what is implication of Outsourcing
= deduction: something that is inferred (deduced or entailed or implied); "his resignation had political implications"
significance: a meaning that is not expressly stated but can be inferred; "the significance of his remark became clear only later"; "the expectation was spread both by word and by implication"
an accusation that brings into intimate and usually incriminating connection
a logical relation between propositions p and q of the form `if p then q'; if p is true then q cannot be false
a relation implicated by virtue of involvement or close connection (especially an incriminating involvement); "he was suspected of implication in several robberies"
wordnetweb.princeton.edu/perl/webwn
Implicature is a technical term in the pragmatics subfield of linguistic coined by Paul Grice. It refers to what is suggested in an utterance, even though not expressed nor strictly implied (that is, entailed) by the utterance. ...
en.wikipedia.org/wiki/Implication_(pragmatics)
In linguistics, entailment is the relationship between two sentences where the truth of one (A) requires the truth of the other (B). This relationship is generalized below.
en.wikipedia.org/wiki/Implication_(logical)
The material conditional, also known as the material implication or truth functional conditional, expresses a property of certain conditionals in logic. In propositional logic, it expresses a binary truth function from truth-values to truth-values. ...
en.wikipedia.org/wiki/Implication_(logic).
= Outsourcing is contracting with another company or person to do a particular function. Almost every organization outsources in some way. Typically, the function being outsourced is considered non-core to the business. An insurance company, for example, might outsource its janitorial and landscaping operations to firms that specialize in those types of work since they are not related to insurance or strategic to the business. The outside firms that are providing the outsourcing services are third-party providers, or as they are more commonly called, service providers.
Although outsourcing has been around as long as work specialization has existed, in recent history, companies began employing the outsourcing model to carry out narrow functions, such as payroll, billing and data entry. Those processes could be done more efficiently, and therefore more cost-effectively, by other companies with specialized tools and facilities and specially trained personnel.
Friday, August 13, 2010
1.Who are they're competitors?
= The competitors of Google are yahoo, YouTube, twitter, Facebook, yelp, Friendster and other social networking site and also the most useful for searching in the Internet are the search engine. But the most competitors of Google is Yahoo. According to www.pcworld.com Google held on to its commanding lead as the preferred search engine in the U.S. in May, processing almost 60 percent of all queries filed, way ahead of its two closest competitors Yahoo and Microsoft. Google nabbed 59.3 percent of search queries, followed by Yahoo in a very distant second place with 22 percent and Microsoft's MSN with 12.1 percent, market researcher Hit wise said Thursday.
- Main Competitors include Yahoo and Microsoft. Yahoo’s Search and Microsoft’s Bing a competitor to Google Search. Has Launched Various Products to counter the dominance of Microsoft like Gmail. Google Earth , Google chrome etc. Will launch a Linux Based operating system which will directly compete against windows.
2. How have they used information technology to their advantage?
= They used information technology to find an accurate information through the technology and users can easily find answer about what they want to search using search engine. Google upgrade their data storage to store more data and information to have more user to visit them. They create some application like Gmail that have 50X more storage than industry average – 25GB of email storage per employee according to Google apps. According to co-founder Larry Page We stand alone in our focus on developing the "perfect search engine," "understands exactly what you mean and gives you back exactly what you want." To that end, we have persistently pursued innovation and refused to accept the limitations of existing models. As a result, we developed our serving infrastructure anddiscovery PageRank™ technology that changed the way searches are conducted. From the beginning, our developers recognized that providing the fastest, most accurate results required a new kind of server setup. Whereas most search engines ran off a handful of large servers that often slowed under peak loads,hours employed linked PCs to quickly find each query's answer. The innovation paid off in faster response times, greater scalability and lower costs. It's an idea that others have since copied, while we have continued to refine our back-end technology to make it even more efficient. The software behind our search technology conducts a series of simultaneous calculations requiring only a fraction of a second. Traditional search engines rely heavily on how often a word appears on a web page. We use more than 200 signals, including our patented PageRank™ algorithm, tocheck the entire link structure of the web and find which pages are most important. We then conduct hypertext-matching analysis to find which pages are relevant to the specific search being conducted. By combining overall importance and query-specific relevance, we're able to put the most relevant.
3. How competitive are they in the market?
= The degree to which a market or industry can be described as competitive depends in part on how many suppliers are seeking the demand of consumers and the ease with which new businesses can enter and exit a particular market in the long run.
The spectrum of competition ranges from highly competitive markets where there are many sellers, each of whom has little or no control over the market price - to a situation of pure monopoly where a market or an industry is dominated by one single supplier who enjoys considerable discretion in setting prices, unless subject to some form of direct regulation by the government.
In many sectors of the economy markets are best described by the term oligopoly - where a few producers dominate the majority of the market and the industry is highly concentrated. In a duopoly two firms dominate the market although there may be many smaller players in the industry.
Competitive markets operate on the basis of a number of assumptions. When these assumptions are dropped - we move into the world of imperfect competition. These assumptions are discussed below.
4.What new services do they offer?
= Ecosystem Services are the processes by which the environment produces resources that we often take for granted such as clean water, timber, and habitat for fisheries, and pollination of native and agricultural plants. Whether we find ourselves in the city or a rural area, the ecosystems in which humans live provide goods and services that are very familiar to us.
Ecosystems provide “services” that:
These services are extensive and diverse … affecting the quality of our land, water, food, and health.
* moderate weather extremes and their impacts
* disperse seeds
* mitigate drought and floods
* protect people from the sun’s harmful ultraviolet rays
* cycle and move nutrients
* protect stream and river channels and coastal shores from erosion
* detoxify and decompose wastes
* control agricultural pests
* maintain biodiversity
* generate and preserve soils and renew their fertility
* contribute to climate stability
* purify the air and water
* regulate disease carrying organisms
* pollinate crops and natural vegetation
5.What makes them so unique?
= There are a number of different kinds of gifts out there today that are considered to be special and given purely for the joy of sharing. One such gift would have to the groomsmen gift, which is mainly given to ensure that the joy of the wedding is not just restricted to the bride and the groom and spread to everyone else as well. If you are considering skipping on this gift, think again, as these are definitely an important gift that you would want to include in the ceremony. There are a lot of reasons for this to be quite an important gift for you to consider, some of which are listed below.
Read more: http://www.articlesbase.com/shopping-articles/groomsmen-gift-what-makes-them-so-unique-2302660.html#ixzz0wcZ0XMcb
Under Creative Commons License: Attribution
6.How competitive are they in the international market?
= The authors examine how firms adapt different components of their marketing strategies in foreign markets compared with their domestic market and how such adaptation decisions influence the firms’ competitive positions and performance in foreign markets. The authors conceptualize that adaptation of a marketing-mix component is a purposeful process that is influenced by a firm’s past adaptation strategy, and they investigate the importance of that marketing-mix component to the firm’s success. The authors propose that the adaptation process helps define a firm’s competitive advantage, which in turn affects its performance in the foreign market. The authors develop hypotheses and propositions and test them with a sample of 183 export firms in Hong Kong.
1.Cio
= Central Intelligence Organisation, the secret police in Zimbabwe
Chief information officer, the head of information technology within an organization
* Chief Innovation Officer, the head of innovation, responsible for innovation management
* Chief investment officer, the head of investments within an organization
* Congress of Industrial Organizations, a former United States trade union federation also known as the Committee of Industrial Organization that merged to form the AFL-CIO in 1955
* The International Olympic Committee (French: Comité international olympique)
* The Central Imagery Office, a predecessor organization of the National Geospatial-Intelligence Agency
* Concurrent Input/Output, a file systems feature introduced in JFS (file system) in May 2003
* Cry It Out, an aspect of the Ferberization technique for solving childhood sleep problems
2.Global Warming
= is the increase in the average temperature of Earth's near-surface air and oceans since the mid-20th century and its projected continuation. According to the 2007 Fourth Assessment Report by the Intergovernmental Panel on Climate Change (IPCC), global surface temperature increased 0.74 ± 0.18 °C (1.33 ± 0.32 °F) during the 20th century.[2][A] Most of the observed temperature increase since the middle of the 20th century was caused by increasing concentrations of greenhouse gases, which results from human activity such as the burning of fossil fuel and deforestation.[3] Global dimming, a result of increasing concentrations of atmospheric aerosols that block sunlight from reaching the surface, has partially countered the effects of greenhouse gas induced warming.
Climate model projections summarized in the latest IPCC report indicate that the global surface temperature is likely to rise a further 1.1 to 6.4 °C (2.0 to 11.5 °F) during the 21st century.[2] The uncertainty in this estimate arises from the use of models with differing sensitivity to greenhouse gas concentrations and the use of differing estimates of future greenhouse gas emissions. An increase in global temperature will cause sea levels to rise and will change the amount and pattern of precipitation, probably including expansion of subtropical deserts.[4] Warming is expected to be strongest in the Arctic and would be associated with continuing retreat of glaciers, permafrost and sea ice. Other likely effects include changes in the frequency and intensity of extreme weather events, species extinctions, and changes in agricultural yields. Warming and related changes will vary from region to region around the globe, though the nature of these regional variations is uncertain.
3.The Advantage of Green
= Green Advantage (GA), the country’s longest-standing green certification for builders and building-related practitioners, offers three certification exams:
* Commercial
* Residential
* Commercial/Residential
Green Advantage Certified Practitioners (GACPs) have passed one or more exams, demonstrating their knowledge of the latest in green building principles, materials and techniques. Green Advantage Certification helps builders get jobs, contractors win bids, and allows building occupants to enjoy healthier, more efficient homes and buildings.
Individual GA Exams™ are offered by Green Advantage nationwide at conveniently located testing centers. While attending a training event is not required to sit for the exam, it is always recommended. Preparatory training courses and workshops are developed and delivered by organizations independent of Green Advantage. Group administered Green Advantage Exams may be coordinated with these events.
4.Effect Of Computers
= As computers have become less expensive they have been purchased by more and more families for their homes. Because of this, many children begin to use computers at an early age. Even if computers are not available in their home, children almost certainly will begin to come into contact with computers in school.
Some adults are amazed by how readily young children use computers. Many children find that using computers gives them a sense of power and accomplishment. And, unlike many adults whose first or primary contact with computers is work related, most children first use computers for entertainment purposes and games. This is by no means the only use that children have for computers. Children also use computers for accessing information, as well as for writing stories and research papers.Many individuals who work at a computer experience eye-related discomfort and visual problems. However, based on current evidence it is unlikely that the use ofcomputers causes permanent changes or damage to the eyes or visual system. This report will review the factors relating to eye and vision problems associated with computer work and provide recommendations for preventing or reducing their development.
5.Data center server
= Our comparisons of server , including VMware, Microsoft Hyper-V, as well as open source and Linux options, can help you find the best technologies for your IT department's needs. Our experts advise on migrating to servers from a physical environment and selecting tools. They share techniques for simplifying server management and data center performance monitoring with Other topics include reducing IT costs by consolidating with using energy-efficiency benefits as part a green data center strategy; reaping advantages of in data center disaster recovery planning; and more.
Friday, July 23, 2010
LAB EXAM
1.What is facebook?
= Facebook is a social networking website intended to connect friends, family, and business associates. It is the largest of the networking sites, with the runner up being MySpace. It began as a college networking website and has expanded to include anyone and everyone.
Facebook was founded by 2004 by Harvard student Mark Zuckerberg and originally called thefacebook. It was quickly successful on campus and expanded beyond Harvard into other Ivy League schools. With the phenomenon growing in popularity, Zuckerberg enlisted two other students, Duston Moskovitz and Chris Hughes, to assist. Within months, thefacebook became a nationwide college networking website.
2.What is advantages and disAdvantages of Facebook?
= Facebook - a popular name among those who are so into it. Individuals who have an account in Facebook are now using more of their time to socialize with other people amidst the distance and lack of time. And even if a community like Facebook serves numerous advantages, it also proves to have certain disadvantages as well. There are now series of improvements in the system just to make up with the shortcomings. Arguments regarding the different advantages and disadvantages of Facebook are stated below.
Advantages
· Allows user search for new and old friends
· Accessible to chosen universities having a high level of security
· Makes it less awkward when communicating with strangers or people you are not familiar with
· Love attraction - can be used as a dating service system
· Makes it easier to join groups having similar likes and dislikes
· Allows members to check students who are taking the same class, living within the same area, or coming from the same academy
Disadvantages
· Overcrowding
· Weakening long distance relationship
· Unsupported by physical adjacency
· Contributes wide-range procrastination
· Rampant addiction
· Stalking is possible
· Acquaintances be labeled as friends
Surely, the disadvantages don't pose a threat to you just by merely looking at it. Someone else has to prove that what users do with their profile is directly in proportion with what can happen to them. A user must understand what he is trying to give out otherwise things might get messy and people will mistook them as someone else.
It is quite obvious that a trade off is happening between the advantages and disadvantages of Facebook. While it increases the communication and connection between friends and the online community it also increases the risk of procrastination and makes it easier for others to stalk a user. Worse, some are actually punished for what they put on their profile and would claim that it was there only for fun.
Despite the above mentioned advantages and disadvantages of an online networking service, it still is gaining demand and popularity among the young crowd. There are about 10,000 students (professionals and young professionals not yet included) who are joining into Facebook every day. This is regardless of the age, race and country. Some are now trying to criticize the status of professionalism of this site whether it's just another fad like other online networking services are.
3.what are the charactirestics of Facebook and why many people engage in this site
= The characteristic of this social networking site are entertaining because of more application.
People who have an account of facebook can store their photos or image, information and can find or search people tha t have an account of facebook. It have more application like Alerts, Business, Chat, Classified, Dating, Education, Events, Fashion, File Sharing, Food and Drink, Gaming, Just for Fun, Messaging, Mobile, Money, Music, Photo, Politics, Sports, Travel, Utility, Video. Facebook applications have detailed descriptions, users ratings and reviews, wiki pages, detailed features, screen shots and a battle for its best used applications that is why many people engage in this site.
4. Can you use facebook in E-commerce? how and Why?
= Social networking site, Facebook, is used by more than 150 million people to share personal information with friends online. The site celebrated its fifth-year anniversary yesterday and is continuing to attract members with demographics that could serve e-tailers well in terms of extending market reach and increasing branding.
Web research firm Hitwise reports that, overall, Facebook was the fifth-ranked Web site in terms of total market share of visits in January 2009. Furthermore, the time spent on Facebook has continued to increase and reached an average visit time of just over 21 minutes in January 2009.
Facebook how-to guide, we will show you how to use two of the business solutions offered by Facebook. First, we'll walk through the steps you need to take to create your own Facebook Business Page (also called a fan page) and then discuss the tasks involved in creating a Facebook Ad campaign, which can be used to send visitors to your Web site or new Facebook Business Page
5.How important facebook in the society today?
There are several social networking sites today, among the popular ones are Facebook, MySpace and Twitter. Most members of these sites are teenagers who just love the company of friends and other people. However, did you know how important social networking sites are?
1. Keeping in touch
By maintaining a profile on these sites, your loved ones, friends and distant relatives don't have to call you everytime just to stay in touch with one another.
2. Job hunting
Several companies in the US and Europe are taking advantage of social networking sites to get competent employees. On the other hand, job applicants take advantage of these sites to post their resume and credentials.
3. Emergency
Friday, July 9, 2010
I feel this can be a competitor for google.. ( http://beta.previewseek.com )
Internet. Some history.
Back in the days of Yore, (lets see that was a whole 8 years ago
maybe), search engines weren't very good. They were better than
nothing, but trying to find things took quite a bit of skill or a
large sense of humor. You could put in a query and almost anything
would come up, and that anything would number in the 10,000's. A
Researcher on the web could use plus and minus signs, quotes and AND
OR logic to wade through the results, getting a bit better listings
for his query, but for the average user, it was still a mess.
Using Google Analytics Aggregated data Google can collect statistics regarding other search engines and how they refer you to sites.
http://photos1.blogger.com/blogger/7938/399/1600/ggraph.0.jpg
In effect what keywords they refer, vs. what keywords others refer. They also can get raw counts in the number of unique visitors and total visitors by referrer
This is only possible because Google Analytics is a centralized web application maintained and operated by Google vs. AWStats another common used alalytics platform which is installed maintained and operated by the webmaster.
* Shared Linux
* Shared Windows
* Virtual Private Server
* Ruby on Rails Hosting
* SBS Hosting
* WebStore
* Virtualized Green Package
WebCare Services
* Website Traffic Analysis
* Website Vulnerability Testing
* Off-site Data Backup
* SEO Services
* Google Adword Campaign Management
NetCare Services
* Cisco Router Configuration
* Network Monitoring Service
* Network Vulnerability Test
* Standby Router Program
Streaming Service
* Audio Encoding Service
* Video Encoding Service
* Webcast Your Audio
* Live Webcast
Obviously, if it was easy to emulate Google, everyone would have done it or would be doing it by now. The more I think about Google, the more and more I think it is going to be impossible to emulate them. Certainly you can steal some of their ideas and what they’ve pioneered and put it to use in your company, but outright copying Google is going to be near impossible.
Having touched on Google’s corporate culture, let’s look at something else that makes Google even more unique: how it grows.
One thing that has become evident to me is that Google grows in an organic fashion, unlike any other company I know of. Google develops tools that are internally useful and then releases them to the world. Google does not develop products to sell to the world. Google does not have external contracts, at least in the traditional sense, as far as I can tell.
from: www.google.com
Sunday, January 17, 2010
Process
Definition
Sequence of interdependent and linked procedures which, at every stage, consume one or more resources (employee time, energy, machines, money) to convert inputs (data, material, parts, etc.) into outputs. These outputs then serve as inputs for the next stage until a known goal or end result is reached.
Wednesday, January 13, 2010
Binary Trees
This article introduces the basic concepts of binary trees, and then works through a series of practice problems with solution code in C/C++ and Java. Binary trees have an elegant recursive pointer structure, so they are a good way to learn recursive pointer algorithms.
Contents
Section 1. Binary Tree Structure -- a quick introduction to binary trees and the code that operates on themSection 2. Binary Tree Problems -- practice problems in increasing order of difficulty
Section 3. C Solutions -- solution code to the problems for C and C++ programmers
Section 4. Java versions -- how binary trees work in Java, with solution code
Stanford CS Education Library -- #110
This is article #110 in the Stanford CS Education Library. This and other free CS materials are available at the library (http://cslibrary.stanford.edu/). That people seeking education should have the opportunity to find it. This article may be used, reproduced, excerpted, or sold so long as this paragraph is clearly reproduced. Copyright 2000-2001, Nick Parlante, nick.parlante@cs.stanford.edu.Related CSLibrary Articles
- Linked List Problems (http://cslibrary.stanford.edu/105/) -- a large collection of linked list problems using various pointer techniques (while this binary tree article concentrates on recursion)
- Pointer and Memory (http://cslibrary.stanford.edu/102/) -- basic concepts of pointers and memory
- The Great Tree-List Problem (http://cslibrary.stanford.edu/109/) -- a great pointer recursion problem that uses both trees and lists
Section 1 -- Introduction To Binary Trees
A binary tree is made of nodes, where each node contains a "left" pointer, a "right" pointer, and a data element. The "root" pointer points to the topmost node in the tree. The left and right pointers recursively point to smaller "subtrees" on either side. A null pointer represents a binary tree with no elements -- the empty tree. The formal recursive definition is: a binary tree is either empty (represented by a null pointer), or is made of a single node, where the left and right pointers (recursive definition ahead) each point to a binary tree.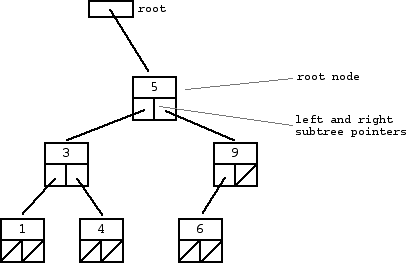
A "binary search tree" (BST) or "ordered binary tree" is a type of binary tree where the nodes are arranged in order: for each node, all elements in its left subtree are less-or-equal to the node (<=), and all the elements in its right subtree are greater than the node (>). The tree shown above is a binary search tree -- the "root" node is a 5, and its left subtree nodes (1, 3, 4) are <= 5, and its right subtree nodes (6, 9) are > 5. Recursively, each of the subtrees must also obey the binary search tree constraint: in the (1, 3, 4) subtree, the 3 is the root, the 1 <= 3 and 4 > 3. Watch out for the exact wording in the problems -- a "binary search tree" is different from a "binary tree".
The nodes at the bottom edge of the tree have empty subtrees and are called "leaf" nodes (1, 4, 6) while the others are "internal" nodes (3, 5, 9Binary Trees
This article introduces the basic concepts of binary trees, and then works through a series of practice problems with solution code in C/C++ and Java. Binary trees have an elegant recursive pointer structure, so they are a good way to learn recursive pointer algorithms.
Contents
Section 1. Binary Tree Structure -- a quick introduction to binary trees and the code that operates on themSection 2. Binary Tree Problems -- practice problems in increasing order of difficulty
Section 3. C Solutions -- solution code to the problems for C and C++ programmers
Section 4. Java versions -- how binary trees work in Java, with solution code
Stanford CS Education Library -- #110
This is article #110 in the Stanford CS Education Library. This and other free CS materials are available at the library (http://cslibrary.stanford.edu/). That people seeking education should have the opportunity to find it. This article may be used, reproduced, excerpted, or sold so long as this paragraph is clearly reproduced. Copyright 2000-2001, Nick Parlante, nick.parlante@cs.stanford.edu.Related CSLibrary Articles
- Linked List Problems (http://cslibrary.stanford.edu/105/) -- a large collection of linked list problems using various pointer techniques (while this binary tree article concentrates on recursion)
- Pointer and Memory (http://cslibrary.stanford.edu/102/) -- basic concepts of pointers and memory
- The Great Tree-List Problem (http://cslibrary.stanford.edu/109/) -- a great pointer recursion problem that uses both trees and lists
Section 1 -- Introduction To Binary Trees
A binary tree is made of nodes, where each node contains a "left" pointer, a "right" pointer, and a data element. The "root" pointer points to the topmost node in the tree. The left and right pointers recursively point to smaller "subtrees" on either side. A null pointer represents a binary tree with no elements -- the empty tree. The formal recursive definition is: a binary tree is either empty (represented by a null pointer), or is made of a single node, where the left and right pointers (recursive definition ahead) each point to a binary tree.A "binary search tree" (BST) or "ordered binary tree" is a type of binary tree where the nodes are arranged in order: for each node, all elements in its left subtree are less-or-equal to the node (<=), and all the elements in its right subtree are greater than the node (>). The tree shown above is a binary search tree -- the "root" node is a 5, and its left subtree nodes (1, 3, 4) are <= 5, and its right subtree nodes (6, 9) are > 5. Recursively, each of the subtrees must also obey the binary search tree constraint: in the (1, 3, 4) subtree, the 3 is the root, the 1 <= 3 and 4 > 3. Watch out for the exact wording in the problems -- a "binary search tree" is different from a "binary tree".
The nodes at the bottom edge of the tree have empty subtrees and are called "leaf" nodes (1, 4, 6) while the others are "internal" nodes (3, 5, 9
BINARY SEARCH TREE
In computer science, a binary search tree (BST) is a node based binary tree data structure which has the following properties:[1]
- The left subtree of a node contains only nodes with keys less than the node's key.
- The right subtree of a node contains only nodes with keys greater than the node's key.
- Both the left and right subtrees must also be binary search trees.
From the above properties it naturally follows that:
- Each node (item in the tree) has a distinct key.
Generally, the information represented by each node is a record rather than a single data element. However, for sequencing purposes, nodes are compared according to their keys rather than any part of their associated records.
The major advantage of binary search trees over other data structures is that the related sorting algorithms and search algorithms such as in-order traversal can be very efficient.
Binary search trees are a fundamental data structure used to construct more abstract data structures such as sets, multisets, and associative arrays.